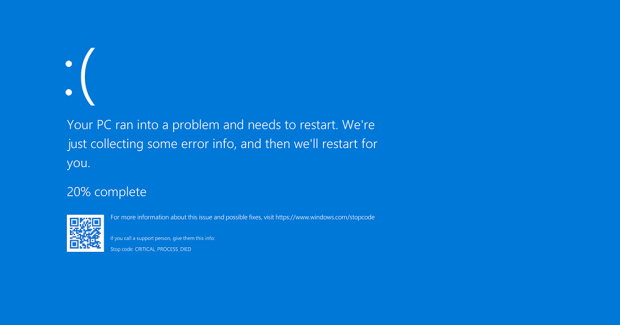
The CrowdStrike update that knocked millions of Windows PCs into boot loop cycles and blue screen of death error (BSOD) messages is truly a historic time for IT chaos, and with chaos comes people wanting to take advantage of the vulnerable.
VIEW GALLERY – 2 IMAGES
An update containing a faulty driver was mistakenly verified and added to CrowdStrike’s production line, which was then pushed out to millions of Windows computers around the globe. The millions of Windows PCs stuck blue screening have disrupted an exponential list of industries and critical infrastructure. For example, airlines were grounded, hospitals were knocked offline, and payment systems have fallen. The outage has disrupted banks, stock exchanges, supermarkets, and more.
Unfortunately, the fix for this problem must be done manually. A user must reboot the affected machine as many as fifteen times to enter Windows Recovery or boot to Safe Mode. From there, the user must locate a file and delete the broken driver. Then, simply reboot. With millions of PCs affected around the world and people searching for a workaround to fix their affected system or systems, users must be careful not to fall for scams claiming to have solutions.
The Singapore Cyber Emergency Response Team (SingCert) has warned of a wave of phishing scams involving people impersonating CrowdStrike staff in phone calls and emails. Additionally, these scams include people posing as independent researchers claiming to have evidence the technical issue is linked to a cyberattack, and they offer remedies for the outage in exchange for money. The warning also mentions people selling scripts to automate the recovery process.
Below is a list of possibly malicious domains that are attempting to impersonate CrowdStrike, and according to the company’s own blogpost users should be aware there is a large uptick in malicious activity following the outage. System administrators could add the below domains to their firewall to block any connections, as connecting to them would likely lead to further complications and potential system vulnerabilities.
To fix the Windows blue screen problem follow the official steps here.
CrowdStrike Scams, Beware!
- Sending phishing emails posing as CrowdStrike support to customers
- Impersonating CrowdStrike staff in phone calls
- Posing as independent researchers, claiming to have evidence that the technical issue is linked to a cyberattack and offering remediation insights
- Selling scripts purporting to automate recovery from the content update issue
Possible Malicious Domains (Scam)
- crowdstrike.phpartners[.]org
- crowdstrike0day[.]com
- crowdstrikebluescreen[.]com
- crowdstrike-bsod[.]com
- crowdstrikeupdate[.]com
- crowdstrikebsod[.]com
- www.crowdstrike0day[.]com
- www.fix-crowdstrike-bsod[.]com
- crowdstrikeoutage[.]info
- www.microsoftcrowdstrike[.]com
- crowdstrikeodayl[.]com
- crowdstrike[.]buzz
- www.crowdstriketoken[.]com
- www.crowdstrikefix[.]com
- fix-crowdstrike-apocalypse[.]com
- microsoftcrowdstrike[.]com
- crowdstrikedoomsday[.]com
- crowdstrikedown[.]com
- whatiscrowdstrike[.]com
- crowdstrike-helpdesk[.]com
- crowdstrikefix[.]com
- fix-crowdstrike-bsod[.]com
- crowdstrikedown[.]site
- crowdstuck[.]org
- crowdfalcon-immed-update[.]com
- crowdstriketoken[.]com
- crowdstrikeclaim[.]com
- crowdstrikeblueteam[.]com
- crowdstrikefix[.]zip
- crowdstrikereport[.]com